Find Business Email Compromise (BEC) Scams

This practice of Business email compromise (BEC) scams is a kind of cybercrime and is used to defraud the company and its assets. A business email compromise is a vast and increasing problem that targets companies no matter the size and spreads all across the industry around the world.
In an era of cloud-based infrastructure email account compromise (EAC) or email account takeover is accelerating threats in cloud infrastructure. EAC is often linked with BEC because compromised accounts are used in an increasing number of BEC frauds and EAC can be considered as other kinds of cyber attacks.
BEC and EAC are probably difficult to detect and prevent from legacy tools, point products, and sometimes on primary but with the help of these practices you can able to prevent it with ease. BEC frauds have exposed many organizations to billions of dollars in potential losses with no expectations to return.
How Business Email Compromise (BEC) Scams Work?
The perpetrator of a BEC scam usually assumes the identity of a vendor, manager, or colleague that the target should be able to trust. The sender requests that the receiver update banking information for upcoming payments, reroute payroll, make a wire transfer, and so forth.
Because BEC attacks don’t employ malware or malicious URLs that can be examined by conventional cyber defenses, they are challenging to identify. BEC assaults, on the other hand, rely on social engineering strategies like impersonation to fool individuals into communicating on the attacker’s behalf.
You can use phishing simulation tool because their targeted nature and large use of social engineering are not fruitful in manual attacks Investigating and remediating these attacks will be difficult and process of time-consuming.
BEC scams use many impersonation techniques like domain spoofing and present them as genuine real domains. These attacks are lethal because domain misuse is a big problem. If you are going to anticipate domain spoofing it will be time and every potential domain looks like spoofing will be a major problem. outside partner can exploits organizations data with the outsiders.
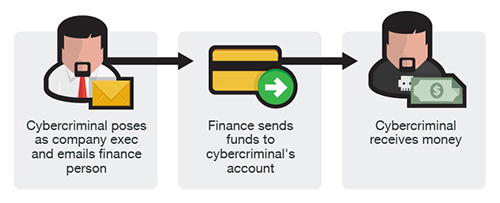
In EAC, the attacker takes over a reputable email account, which enables them to initiate BEC-style attacks. However, in these situations, the attacker isn’t merely pretending to be someone; in reality, the attacker is that person.
BEC and EAC require a people-centric defense that can prevent, detect, and respond to a wide range of BEC and EAC approaches because they prioritize human fragility over technical vulnerabilities.
How to Protect Against Business Email Compromise (BEC) Scams Attacks
If the BEC attack is successful in your organization it could be extremely costly and damaging to the reputation of an organization. Follow this security precautions to minimize attacks:-
Anti-Phishing Protections
Use anti-phishing solutions to protect against BEC emails that are a type of phishing. This attack is dangerous so your solutions should be capable of identifying the red flags of BEC emails red flags can considered as (addresses that don’t match the sender’s addresses) and also solution should use machine learning to find out language for indications of an attack.
Employee Education
Since employees are the target of BEC attacks, email security awareness training is essential for cybersecurity. Personnel should trained on recognize and respond to a BEC assault to lessen the threat of this type of phishing.
Separation of Duties in Business Email Compromise (BEC) Scams
BEC attacks aim to fool staff members into executing a risky activity (such as delivering money or private data) without first confirming the request. Requiring independent verification from a second employee can help reduce the likelihood of a successful assault by implementing policies for certain behaviors.
Labeling External Emails
BEC attacks commonly try to imitate internal email addresses using domain spoofing and represent them as lookalike domains. The best way can be configuring email programs to label emails that are coming from outside of the company premises as “external email” which can help to prevent this tactic.
Read More:- Easily connect Gmail to GoDaddy domain [Instant Solution]
Conclusion
Business Email Compromise (BEC) Scams are a major combination of attacks to trick their victims and a planning attack to gain access to a business organization. This attack consists of a spear-phishing attack in conjunction with some form of malware.
Don’t waste your time thinking twice about taking prevention because business email compromise attacks are dangerous and, if attacker stays undetected.
Hackers can spend time studying important characteristics of the organization, from every corner like information about vendors and billing systems and alikeness habits and attributes of employees and outside executive partners.